Last Logged On User Registry
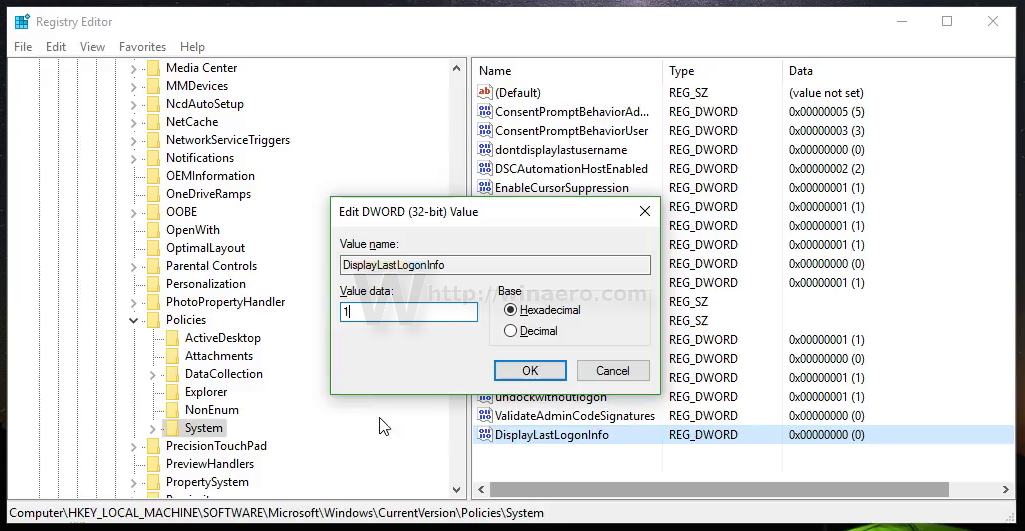
If you have enabled the classic interactive login in Windows 7, after that Windows will show the last Iogged in username éverytime it begins. This will be a useful feature because if the same user records on again, then he/she has to enter just the password. But some users may not including the function as it will reveal the identity of the usér who last utilized the pc.
If you do not including this feature, after that you can turn off it.
Login Trouble - Many users do not know how to switch user accounts, and they may spend 30 minutes trying to login before they call you for help! To change the last logged in user at the Windows XP login screen, simply edit the following registry entry and restart the computer. Jetbrains pycharm v1.2.1 cracked [rtspj]. Just add the username to the entry (only the username, not the. It may be better to pull the last 5 logged on users, and then you would have a better idea of what's going on. 2.Use this code to get the currently logged on user: (gwmi -class win32computerSystem -computer 'ComputerName').username 3.A different and unique way of getting the last logged on user is to use the last write access time on the user.
Interactive logon: Don't screen last signed-in. 2 a few minutes to read. Members.In this articleApplies to. Home windows 10Describes the greatest practices, location, beliefs, and security considerations for the Interactive logon: Wear't display last signed-in security policy environment. Before Home windows 10 edition 1703, this plan setting was called Interactive logon:Do not display last user title. ReferenceThis protection policy environment decides whether the name of the Iast user to log on to the device is shown on the Safe Desktop computer.If this plan is enabled, the complete name of the Iast user to successfuIly record on can be not displayed on the Secure Desktop, nor is definitely the user's logon floor tile displayed.
- Windows Registry Last Logged On User: Get Rid of PC Issues in 3 Easy Steps with Guaranteed Results ★ WINDOWS REGISTRY LAST LOGGED ON USER ★ Free Diagnose Your Computer For Errors.Boost PC, Registry Cleaning, Malware Protection & More. Speedzooka Softonic Windows Registry Last Logged On User The second is called MalwareBytes Anti Malware is a free program.
- Jan 28, 2010 User who forgotten to change the user ID on display can accidentally lock other user out if trying too many incorrect password. Windows provides a registry or group policy trick that instruct Windows not to remember and display the last user name who logged in. Follow the steps below to tweak the registry setting or group policy.
Furthermore, if the Change user function is utilized, the full title and logon floor tile are not really shown. The logon screen demands a competent domain account title (or local user name) and security password.If this plan is impaired, the complete name of the Iast user to record on is displayed, and the user's logon tile is shown. This behavior is definitely the same when the Change user feature is utilized. Possible beliefs.
Enabled. Impaired. Not really definedBest practicesYour implementation of this plan is dependent on your security specifications for displayed logon details. If you possess products that store sensitive information, with screens displayed in unsecured locations, or if you have got products with delicate information that are usually remotely utilized, exposing logged on user's i9000 full names or domains account names might contradict your overall security policy. LocationComputer ConfigurationWindows SéttingsSecurity SettingsLocal PoliciesSecurity Choices Default beliefs Server kind or Group Policy target (GPO)Default valueDefault site policyDisabledDefault domain control policyDisabledStand-alone server default settingsDisabledDomain control effective default settingsDisabledMember server effective default settingsDisabledEffective GPO default settings on client computersDisabledPolicy managementThis section describes functions and tools that are usually obtainable to help you take care of this policy. Reboot requirementNone.
Adjustments to this policy become efficient without a gadget restart when they are usually saved in your area or dispersed through Group Policy. Plan discord considerationsNone. Group PolicyThis plan environment can become set up by making use of the Group Policy Management System (GPMC) to end up being dispersed through Group Policy Items (GPOs). If this policy is not really included in a dispersed GPO, this plan can be configured on the regional personal computer by using the Community Security Plan snap-in. Security considerationsThis section identifies how an attacker might exploit a feature or its construction, how to carry out the countermeasure, and the probable negative consequences of countermeasure implementation. VulnerabilityAn attacker with accessibility to the gaming console (for instance, somebody with bodily entry or somebody who can connect to the gadget through Remote Desktop Session Web host) could view the name of the Iast user who Iogged on. The opponent could then try to imagine the password, use a dictionary, or use a brute-force assault to try to log on.
Last Logged On User Registry Windows 10
CountermeasureEnable thé Interactive logon: Do not screen last user name setting. Potential impactUsers must generally sort their user titles and security passwords when they sign on in your area or to the site. The logon tiIes of all Iogged on customers are not displayed.
Associated topics.Responses.
Hi guys,yes ! I also undérstood this correctly át the first pIace.
Last Logged In User Registry
Really standard solutions. Tamil serial actress hot scene.





